Black Desert Online - Overview
Contents
After spending many hours on reverse engineering Black Desert Online I noticed that this would be a great blog topic.
So, have fun reading :)
Introduction
What is BDO?
Black Desert Online (BDO) is a fairly recent MMORPG. It was first released 2015 in south korea, the EU/US release followed in 2016.
It's like most other MMORP's but with some different aspects. I won't go into details, it should be easy to find out about BDO by yourself.
I just want to mention one thing: There is only one central market, so there is no P2P item exchange nor selling.
Why BDO?
- I play it.
What do I want?
- Clean up with some speculation:
- How does the RNG work?
- How the heck is the (market) bidding working?!
- Increase available tools for players:
- Statistics for market sales
- Notifications for market items
Basic Research
Before we start looking into reverse engineering BDO, it's helpful to see what other people did so far.
So, what can we look into?
There are basically two sources for obtaining data:
- the server
- the client
Some data maybe exclusively available on the server. One big candidate for that is the RNG.
(My) rule of thumb is to start with the easiest option available (easiest for me) and switch to the next when you're stuck. Which is in our case the client as we can simply download the complete client.
The data in the client can be split further into some categories:
- Static data (files)
- Executable code
- Assets / resources
- Dynamic data
- Process memory
- Network data
- Saved data (in our case most likely only on the server)
With that in mind we look through tools for BDO and try to guess where they got their data from.
Existing BDO Tools
-
BDO Database bddatabase.net
Database with Items, Quests and everything else -
Alchemy / Cooking Calculator and Node Manager www.bdodae.com
Recipes for alchemy / cooking and margin calculation (requires current market prices of items). -
BDO Planner (Gear) bdoplanner.com
-
Fail Stack Optimizer www.blackd.de/failstacks
Available Data
The existing tools suggest that it must be possibly to extract, at least to some degree, static assets data from BDO (or they have plenty of time to retype all data). But none of them seems to have live data. So it's unlikely BDO offers an (maybe undocumented) API for their data.
So I started looking around in the game folder to find the data some of the tools are using. The search revealed that everything except binaries, cache and logs resides in .PAZ files.
Detect PAZ File Format
So first of all it's a good idea to find out if this is a common file format.
Detecting a files format:
-
Using
filecommand on Linux or BSD / OS X.
-> Not available on Windows :( -
Try uncompressing the file: Open with e.g. 7-zip.
-> Not a valid file or unknown by 7-zip. -
Search the internet for ‘.PAZ’ file extension.
-> Looks like a BDO specific file format. (Keep in mind that BDO uses it's own game engine.)
After scrolling further through the search results I found some tools for unpacking those files:-
Unpacker:
https://github.com/kukdh1/PAZ-Unpacker -
BDO (PAZ) Modding Tools:
https://www.undertow.club/threads/black-desert-online-modding-tools.9197/
-
So now we could unpack the static game assets. As I'm currently not interested in the static stuff I'll just put it on my list of things I found out about BDO and keep digging around. This could be handy later, who knows.
Cheating Tools (Process Memory)
Cheating tools tend to work with the process memory and could tell us how easy it is to bypass the Anti-cheat software. And maybe they already have access to some of the data I'm interested in.
Searching around revealed no available cheats except some bots. Besides I don't like cheaters I definitely won't support people selling Cheats / Bots so I won't link them here.
But there are some people who claim that most of the game logic is executed on the client, such as:
- position (moving speed / high)
- skill cooldown
That would be horrible and as I know too many companies / developer failing with such stuff it's not that unlikely. So I'll put that on my list of things I want to prove.
Before considering the Process Memory as your starting point you should definitely have a look at the Anti-cheat software which is in case of BDO is XIGNCODE3:
Looking at their list of features seems like they are undefeatable, but thats what every Anti-cheat software wants you to think (they want to sell it). Searching on cheat forums gives as a more realistic list of features (Source):
They can detect:
-API hooks
-Filenames
-Files on your drive via USN Journal & Prefetch
-API call return addresses
-Sigs of detected cheats
-Windowtitles
-Strings
-DNS cache entrys
-Icon hashes
-linked modules
-code injection at runtime
For only process memory analysing purposes that should be no big problem, but beside the detections they claim to protect the game against manipulation:
Reject game process memory accessing
Reject game process handle accessing
Reject game process message transmission
Reject game process keyboard/mouse input transmission
Reject game window GDI accessing
Reject debug interrupt handler modification
Reject calling kernel function directly
Reject stealth process/module/driver
Reject kernel/user mode debugging
Those on the other hand are looking like a show stopper. I may write an article on Anti-cheat software and go into some details on how they are basically working and how they can be bypassed.
But for the current project I'm going to move memory analysing at the end of my list of things to try.
Network Protocol
Next thing on my list are the network protocols.
The easiest way to get a basic idea of what BDO is doing is looking at the network traffic itself. So I fired up Wireshark and scrolled through the packets. To minimize the unrelated traffic I ran BDO inside a VM, in my case VirtualBox.
BDO Launcher
My first target was the BDO Launcher:
You may wonder what I was looking for in the traffic. My first step is to scan everything and try to spot interesting stuff, that may already give me some clues what BDO does.
What caught my eyes was the following:
- DNS
- HTTP
- TCP without HTTP
- TLSv1.2 (most likely HTTPS)
Except the TCP only packets it looks MUCH like a web browser. This could be abundant, not for the data I'm looking for but maybe for understanding how the BDO infrastructure works.
I'll put the analysis of the network traffic data in a separate article “Black Desert Online - Network Protocol Basics” so I don't go beyond the scope of an overview.
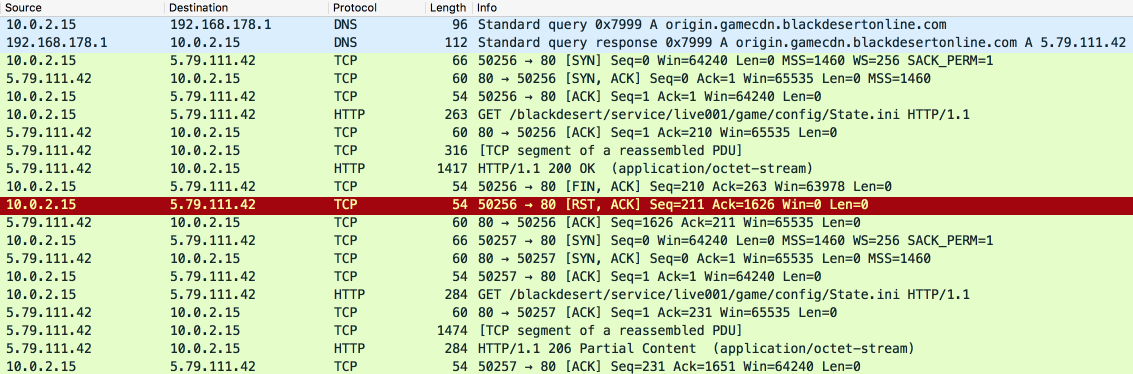
BDO Game
But there is more, the actual game I'm interested in:
(Note: I had to bypass an Anti-VM check, that will be covert in Executable Code.)
Now only one TCP connection is left that caught my attention:
(Note: There were still some HTTP and HTTPS requests, but they belong to XIGNCODE3 so I'll skip them here.)
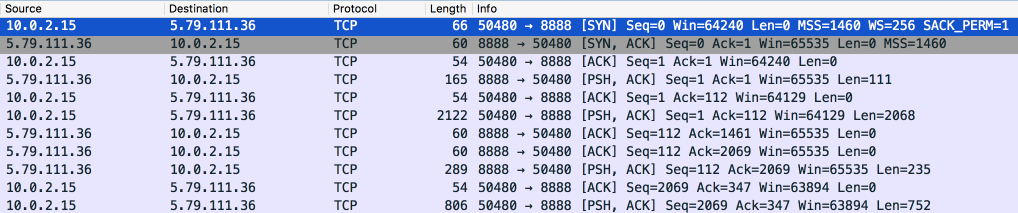
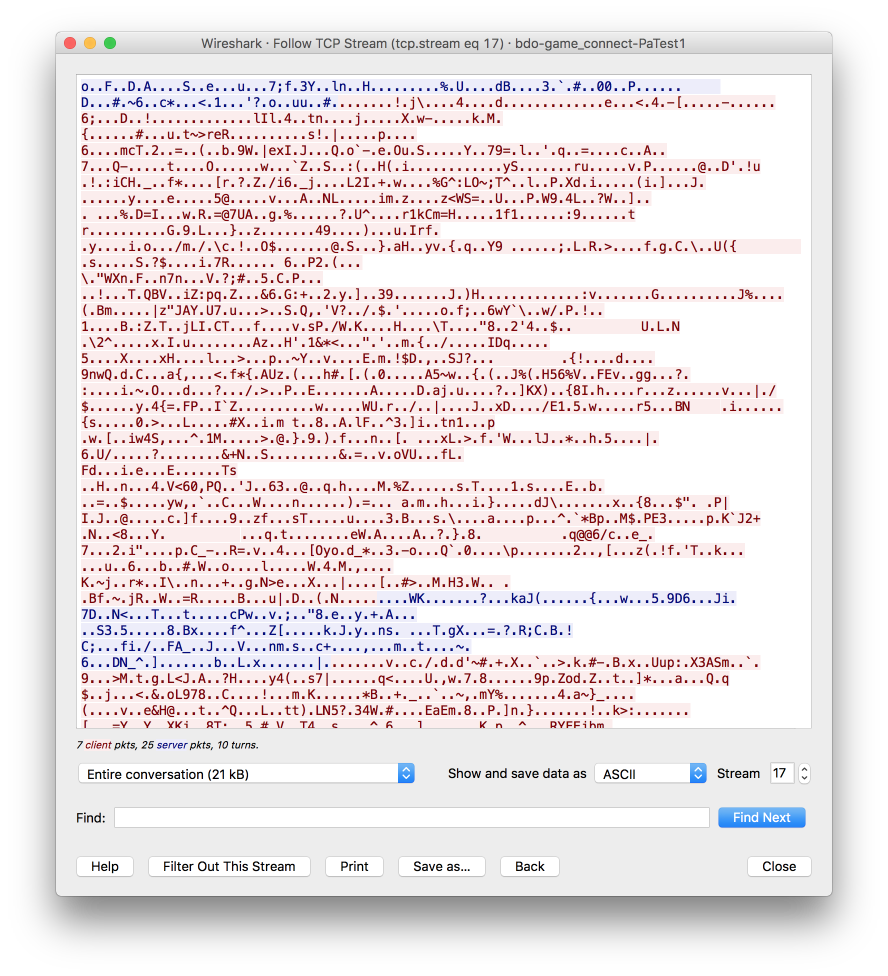
Wireshark has some great functions for analysing traffic, for TCP they have “Follow -> TCP Stream”:
That looks like rubbish, even when I scanned the whole stream I cloudn't find any plain text.
That can have multiple reasons:
- The stream is compressed.
- The stream is encrypted.
- The protocol uses a very strange text encoding.
An easy way to guess if they are using any kind of encryption is to gather multiple tcp streams and compare them. If they are using an (good) encryption it looks like pure randomness.
When I connected to the server multiple times it sends random looking data except the first 5 bytes, which could be the length of the packet and / or packet type. So this looks much like encryption to me, could be a key exchange or something similar.
Maybe someone else already figured that out for me, turns out someone did:
But that code is from around the time of the public EU/US release, so it's possibly outdated. On the other hand they managed to decrypt the packets with Rijndael (AES).
That supports my theory of an encryption.
Comparing the current packets with the structure in the PacketParser.cs it's pretty clear that the packets i captured do not match that structure in any way.
Also the developer(s) state in their open source BDO server project DesertProject:
Packet cryptography was patched on May 4th (2016), awaiting for people willing to update this project.
That was the point were I moved the Protocol Analysis down on my list of things to try.
Executable Code
Maybe analysing the executable could give some hints on the used encryption and key.
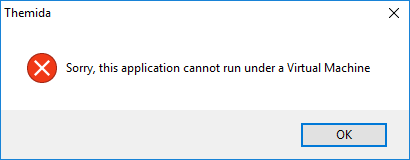
As I already came across the Anti-cheat software and an Anti-VM check it's possible they protected their executable against analysis.
The Anti-VM check error directly shows that it is part if Themida:
You may be interested in how I bypassed the Anti-VM check of Themida:
- open
regeditand - delete any key (folder) containing
VBOXinHKEY_LOCAL_MACHINE\HARDWARE\ACPI\DSDT\, - empty the values of
HKEY_LOCAL_MACHINE\HARDWARE\DESCRIPTION\System\SystemBiosVersionandHKEY_LOCAL_MACHINE\HARDWARE\DESCRIPTION\System\VideoBiosVersion.
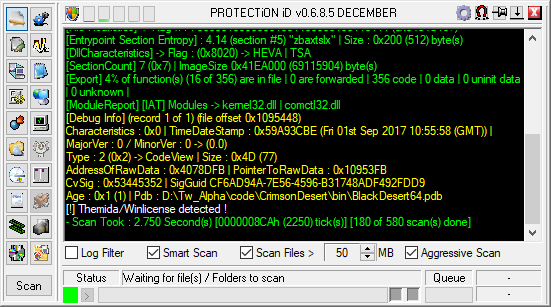
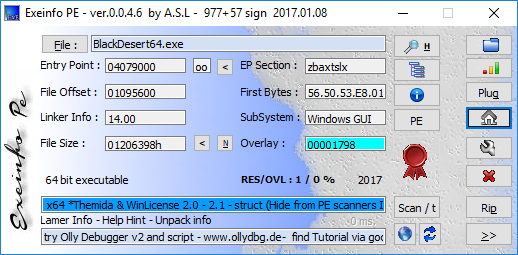
It's always a good idea to throw a protection analyser at the executable.
ProtectionID and exeinfo are usually doing great jobs:
Both also detect Themida which makes your life hard doing reverse engineering of machine code. Packer tend to not only obfuscate the executable but also protect it against debugging and sometimes even more. So that was the point I also moved executable down on my list.
Next step(s)
Now I'm out of things to try on the “easy” level on my list.
I decided to continue on analysing the executable as I had some ideas in mind to go on. Also I tried analysing packed executable code before and never succeeded so that's on of my long term goals I could now achieve.
If you missed it, the next article will be about basic network analysis I already did at this point:
Author Simon Wörner
LastMod 2018-06-06
License

This work is licensed under a Creative Commons Attribution-NonCommercial-ShareAlike 4.0 International License.